Hypervisor
A hypervisor is a powerful software that enables the creation of virtual machines, enabling the seamless operation of multiple operating systems on a single physical server. By doing so, it greatly enhances resource optimization, data security, infrastructure uptime, and scalability.
Hypervisors can be categorized into two types: those that run directly on physical hardware and those that function as a software layer application. In a virtual private server (VPS) environment, hypervisors play a crucial role in constructing, isolating, and efficiently allocating resources among various virtual instances.
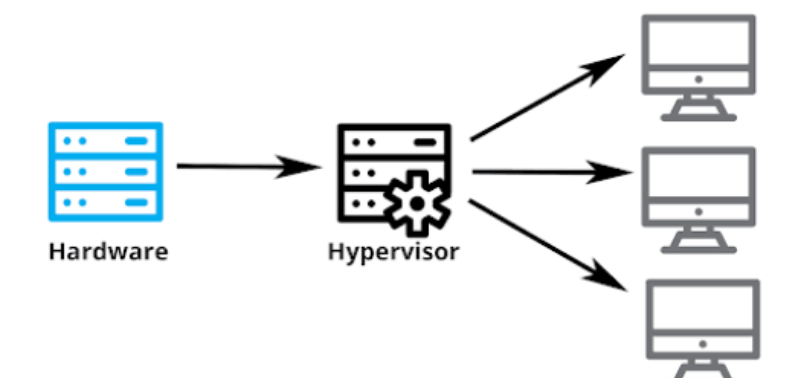
How Do Hypervisors Work?
A hypervisor or a virtual machine monitor (VMM) creates an abstracting layer between physical hardware and software. It pools computing resources from the host, including the CPU, RAM, and storage.
A virtual machine accesses the hardware resources by sending the host machine a request, which the abstracting layer will translate. To facilitate communication and data transfer, the hypervisor uses various methods, including an API call.
It assigns each virtual machine a guest operating system (OS), CPU, RAM, and network allocation based on the request. Since the hypervisor allocates resources dynamically, it can redistribute hardware to different instances based on the requirements.
Independent resource allocation also creates an isolation layer between instances. It allows users to install their own operating system and software without affecting other virtual servers. For example, users can install different operating systems from the host, like FreeBSD with a Windows Server.
Moreover, isolation helps improve security since running risky Linux commands on a VM won’t affect others. In addition, security flaws and cyber attacks on a virtual machine won’t impact the others. If one operating system fails, others will keep running without interruption.
Significance of Hypervisor
A hypervisor offers the opportunity to establish a cost-effective IT infrastructure. Instead of operating multiple physical servers, web hosts have the ability to deploy a single machine that houses numerous virtual instances for numerous users or applications.
The utilization of multiple physical servers can result in the wastage of computing resources, as they cannot be repurposed.
Hypervisors, on the other hand, allow web hosts to seamlessly allocate unused hardware to another instance, thereby optimizing usage and enhancing system performance.
In addition to this, hypervisors bring forth various other advantages, such as simplifying the scaling of hosting infrastructure to accommodate heavier workloads.
For instance, it becomes possible to swiftly allocate a new virtual instance with dedicated virtual resource allocation to execute a fresh task.
Furthermore, the migration of virtual machines to another host with the same hypervisors can be effortlessly accomplished without encountering any compatibility issues.
This capability empowers users to transition to a higher-performance machine without the need for extensive reconfiguration of the virtual environment.
Classification
Depending on the abstraction layer position, there are two hypervisor types – type 1 and type 2 hypervisors. Both have the same purposes but differ in use cases and benefits.
Type 1Bare-Metal Hypervisor
Type 1 bare-metal hypervisors are designed to run directly on physical hardware, enabling the creation and management of guest operating systems.
By scheduling the allocation of resources directly to the host, these hypervisors minimize latency and enhance overall performance. These hypervisors function as lightweight operating systems. It is capable of dynamically allocating resources to fully utilize the hardware capacity of the host.
This means that each virtual machine will only encounter limitations when the workload surpasses the hardware’s resource constraints.
This not only simplifies the process but also enhances security. It reduces the potential attack surface.
They are commonly utilized in enterprise data centers and service provider infrastructures, such as web hosts, due to their superior performance.
However, they may not be suitable for new users due to the complexity of the setup process.
Notable examples of type 1 hypervisors include Microsoft Hyper-V and VMware vSphere, while free options include the open-source Kernel-based Virtual Machine (KVM) and Oracle VM.
Type 2 Hosted Hypervisor
The conventional operating system hosts the type 2 hypervisor, causing a slower and less efficient process as it doesn’t directly schedule VM resource allocations against the underlying hardware.
Some type 2 hypervisors lack dynamic computing hardware allocation, leading to less flexible resource optimization and management.
For instance, assigning a specific amount of RAM to a virtual machine results in a fixed consumption, such as 8 GB.
The security of this hypervisor architecture is compromised compared to bare-metal, as it offers a lower isolation level.
A security vulnerability in the host operating system can also jeopardize virtual instances.
Despite its drawbacks, hosted hypervisors are easier to set up and manage. Users can install the virtualization technology as a software application on a personal system, similar to other computer programs.
This hypervisor type is well-suited for running virtual machines with different operating systems for testing or development, with popular examples including Oracle’s VirtualBox, VMware Fusion, and Windows Virtual PC.
Essential Characteristics of Hypervisors
Hypervisors have several crucial features for creating a virtual server hosting infrastructure. Some of the most important ones are:
- Hypervisors empower users to create multiple isolated virtual instances on a single physical machine, optimizing costs and enhancing workload distributions.
- Dynamic allocation of server resources between virtual instances becomes achievable through hypervisors, allowing the utilization of computing power surpluses for a more stable performance in other environments.
- Snapshotting, a feature of hypervisors, captures the virtual machine’s system state and configurations at a specific time. This establishes a restore point for users to effortlessly recover their data after accidents or when cloning server instances.
- Facilitating seamless data migration, hypervisors enable users to move a virtual instance to another physical host without disrupting running processes or causing downtime. This feature also serves as a failover system, swiftly switching the failed system to a healthy server.
- System administrators can efficiently allocate and reallocate the hardware resource pool to different instances through hypervisors. Additionally, they can conveniently monitor the resource consumption of multiple instances in one place using the hypervisor software.
Hypervisor Use Cases
Let’s dive into the uses of Hypervisor
Resource Segmentation
It lets you divide computing resources like CPU cores, RAM capacity, storage space, and bandwidth in a controlled and isolated manner.
In a VPS hosting environment, it ensures each user gets equal allocation. It is also useful for running different tasks and services on a single server. It guarantees that each process receives enough resources to operate properly.
Controlled resource allocation and isolations also help prevent interferences between applications.
Otherwise, it may lead to performance degradation and instability, harming your service’s usability.
Moreover, you can repurpose other processes’ resource allocations for high-priority or urgent tasks.
For example, you can prioritize the computing power for an intrusion detection system during a security-critical incident.
Cloud Computing
Cloud computing providers utilize hypervisors to offer infrastructure as a service (IaaS) by abstracting their servers.
This technology allows them to provide virtual environments that are isolated and on-demand for hosting users’ applications.
Users can host all their necessary applications in separate virtual instances within the same server, including user-facing services, databases, runtimes, middleware, and guest operating systems.
Hypervisors also make the infrastructure easily scalable, allowing cloud providers to quickly provision new virtual machines for users who want to deploy new applications.
Despite being multi-tenant, the hypervisor’s isolation enables users to freely configure and manage their virtual servers, set hardware allocations according to their needs, and easily migrate to another infrastructure.
Server Consolidation
Consolidation aims to minimize the number of physical machines to create an infrastructure and optimize resource usage.
Users can do so by leveraging hypervisors’ server virtualization capabilities to create multiple virtual instances with dynamic hardware allocations.
In addition to saving costs, consolidation reduces power consumption and speeds up the system provisioning process.
Moreover, it provides a single point of administration using the hypervisor management software like Red Hat’s virtual machine manager.
Consolidation also lets you easily scale the hosting infrastructure. Instead of setting up another physical machine, VM deployment lets you easily create a new isolated environment to run a dedicated workload and application.
Disaster Recovery
System administrators commonly employ hypervisors for disaster recovery and data protection.
Virtual machines, in addition to snapshot features, possess portability and hardware-agnostic qualities, enabling seamless adaptation to other systems without compatibility issues.
Hypervisors provide a replication capability, allowing system administrators to mirror live virtual machines to backup servers. Some also replicate data in real-time, minimizing potential data loss.
These capabilities enable users to swiftly move virtual machines between hosts in case of system failure, ensuring continuous uptime.
In the event of an accident on the live machine, the hypervisor triggers automatic failover, repurposing the secondary system as the new main host.
Backup virtual servers can be set up on the same machine or a remote system in another geographical location, aiding in maintaining uptime, especially in the face of natural disasters.
Development and Testing Environments
Hypervisor’s isolation allows developers to set up a separate development and testing environment easily. They can do so by creating a virtual machine on the same server or in their local systems.
It enables developers to accurately test new changes to their services or applications without affecting the live server. Moreover, they can determine the ideal resource allocations for the applications before deploying them live.
Setting up a virtual development area is simple since hypervisors let users clone VMs to replicate the live environment. It ensures matching configurations and dependencies between two instances, maintaining the testing accuracy.
The virtual machine’s snapshot and rollback features also help improve development efficiency. Instead of manually reverting the changes, developers can easily restore the system to its previous state when encountering errors.
Virtual Desktop Infrastructure (VDI)
A hypervisor allows users to run multiple guest operating systems in a server to create a virtual desktop infrastructure (VDI). It provides users with remote desktop environments, which they can access using a secure protocol.
VDI improves applications and data accessibility since users can manage them anywhere by connecting to the virtual desktop. In addition, you can use any device to access the remote instance.
Regardless of their device’s specifications, users can enjoy the host server’s full hardware capabilities since the workloads run remotely. Moreover, all data resides in a centralized location, minimizing security risks when the endpoint devices are compromised.
Due to these benefits, enterprises use VDI to enable remote working. Instead of provisioning each user with a dedicated device, businesses can save costs and effort by setting up a VDI.
It also simplifies infrastructure management as the system administrator can manage all systems directly from the host machine.
Read More ; Understanding VPN
For more updates follow us on Meta, X, Instagram .