Read this article to learn ‘How To Keep RDP Safe?’.
To gain remote access, the Remote Desktop Protocol (RDP) is commonly utilized. System administrators utilize the Remote Desktop Protocol daily, and it is a popular protocol.
Non-technical users can connect to remote servers using the Remote Desktop Protocol (RDP). Remote desktop protocol (RDP) enables users in the technical field to connect to a remote server from a different place and perform tasks there.
As potent as a remote desktop protocol may be, it can also expose the server to risks. Remote desktop protocol security is a topic we will cover in-depth in this blog post.
Because Remote Desktop sessions are encrypted, no one on the server can hear or see what you’re doing. However, previous versions of the remote desktop protocol are vulnerable due to a weakness in the encryption of sessions.
By exploiting this risk, a third party could intercept your session and gain access to your information.

How To Keep RDP Safe?
In a perfect and well-managed environment, the remote desktop protocol functions flawlessly. The remote desktop protocol only provides standard encryption and safety options by default.
Businesses that rely solely on these settings for safety face unacceptable levels of danger when they’re only employed in this regard.
SSL/TLS can, nevertheless, be used to secure Remote Desktop in all Windows editions. With Remote Desktop, even though it is more safe than VNC, it is still possible for an administrator to gain access to a system from a far-off location and expose themselves to security threats.
There is just one type of network in which remote desktop protocol can be utilized, and that is a LAN. Profiles for different Windows versions are available for remote desktop protocol hosts along with a listening port.
Once they have this information, cybercriminals can use the remote desktop protocol to gain unauthorized access, through the execution of the following types of attacks:
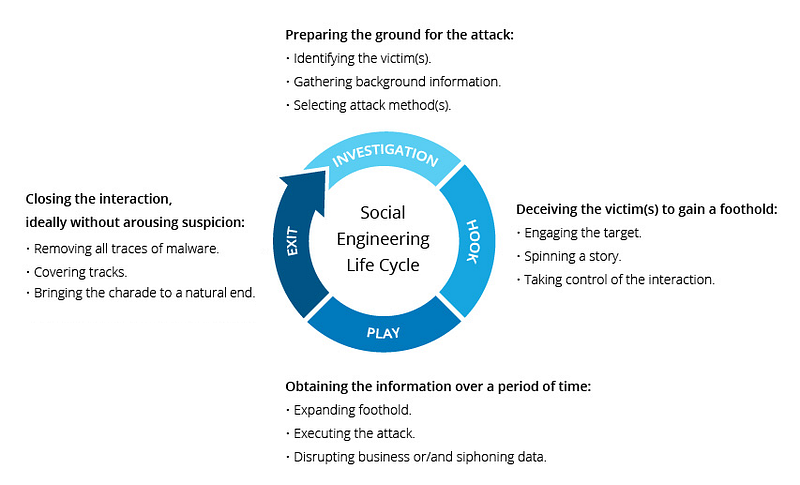
- Social engineering: Persuasion through the use of deceptive methods such as social engineering can lead to the acquisition of sensitive data, access, or assets. Cybercriminals utilize “human hacking” scams to trick unsuspecting individuals into disclosing their information, distributing malware, or granting unauthorized access to their systems. Attacks can occur virtually, in person, or through any other method.
2. Missing safety patches: Software developers frequently roll out security patch updates to all systems running the software that requires them. Delaying patches is a result of security holes and vulnerabilities not being found until after a significant upgrade or even before a new piece of software goes live. Patches for security holes that weren’t covered by a large software upgrade or first software installation are the primary objective of a safety patch up-gradation.
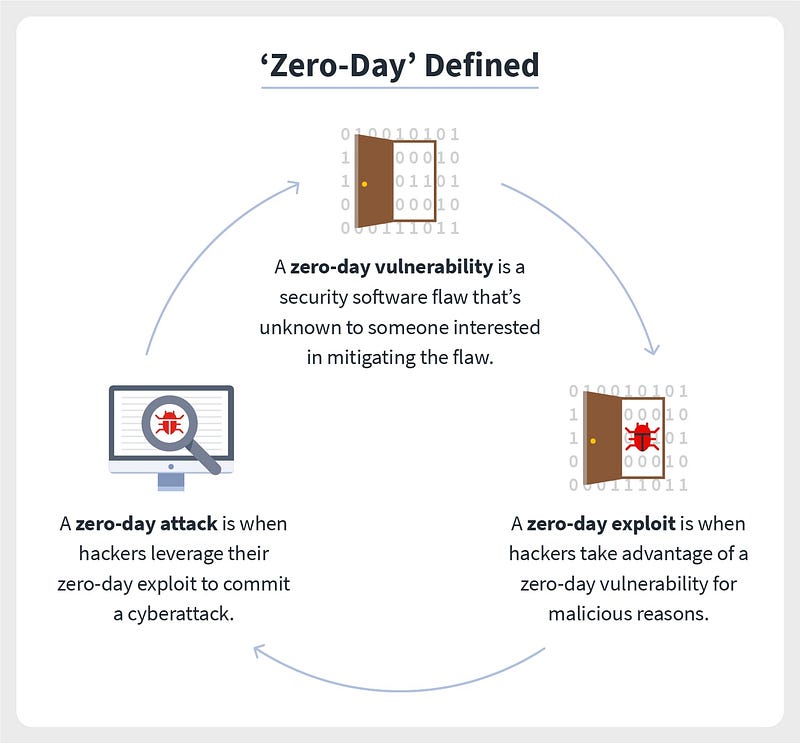
3. Zero-day exploits: Zero-day (0day) exploits are cyber attacks that target a security flaw in a software that is new to the software vendor or antivirus software providers. An attacker discovers a software flaw before anyone else, writes an exploit, and then utilizes it to launch an attack. Because there are no safeguards in place, these attacks are almost certain to be successful. As a result, zero-day attacks are a significant safety risk.
4. Credentials on the dark web: Data stole by fraudsters, like personal banking details, social security numbers, and digital credentials are traded on the dark web. The dark web has over 24 billion compromised credentials, some of which are so easily cracked that the accounts they safeguard might be hacked in under a second.
5. Insecure password management: When it comes to privacy, internet safety, and information safety, strong passwords cannot be overstated. Every password should be distinct, difficult, and lengthy for each service. Strong encryption is provided by a password manager.

What are the precautions to keep RDP safe?
Precautions to keep RDP safe
We have listed all of the precautions you should take to keep your remote desktop protocol safe below:-
Never use the same password twice.
Two-factor authentication should always be used.
Updating your software and computer should be done regularly.
Make use of firewalls to keep out unwanted visitors.
Encryption at the network level must be enabled.
Limit the number of people who can access the system using Remote Desktop.
Ensure that you have a lockout policy in place.
Restriction of direct remote desktop protocol access to clients and servers should always be considered.
It is always best to connect to RDP Gateways.
When using Remote Desktop, make sure to adjust the port number.
Tunnel the Remote Desktop sessions through IPSec or SSH.
Take advantage of current administration tools to log and configure RDP.
Always use the Windows Firewall to prevent RDP access.
VNC is the only method to go with (Virtual Network Computing).
Always use a powerful anti-virus program.

CONCLUSION
After reading this article, you might have got a good idea about, ‘how to keep RDP safe?’. You can also read this article to learn about, ‘What is Remote Desktop Connection Manager (RDCMan)?’.
Visit our website of amazingrdp.com to learn how to buy cheap RDP, Admin RDP, and private RDP. We provide safe as well as cheap RDP services.
You can also visit this website to learn about cheap RDP and dedicated RDP.
We have gone through a few of the best ways to keep your RDP sessions safe in this article. Strong passwords and two-factor verification are just some of the measures you may take to protect yourself online.
Thanks for reading, and hopefully it will help keep your system safe. But if you have any questions regarding any of these, please feel free to ask us.