Open ports in Ubuntu 2022 – How it works
Introduction:
In the world of networking and cybersecurity, open ports play a pivotal role in enabling communication between devices over a network. If you’re using Ubuntu 2022, understanding open ports is essential for maintaining a secure and functional system. In this guide, we’ll delve into what open ports are, how they work, and how to manage them effectively on an Ubuntu system.
What Are Open Ports?
In simple terms, a port is like a door through which data can enter or leave a computer. Ports are numbered and each number corresponds to a specific service or application. An open port is a port that is actively accepting incoming data packets, allowing communication to occur between your computer and other devices on the network or the internet. It’s important to note that not all ports need to be open – in fact, keeping unnecessary ports closed enhances your system’s security.
How Open Ports Work:
When an application or service wants to communicate over a network, it listens on a specific port for incoming data. When data packets arrive at a specific port, the operating system’s networking stack determines which application or service should receive the data based on the port number. For instance, web servers typically listen on port 80 for HTTP requests and port 443 for HTTPS requests.
Buy Chep Linux Server
Managing Open Ports in Ubuntu 2022:
1. Firewall Configuration:
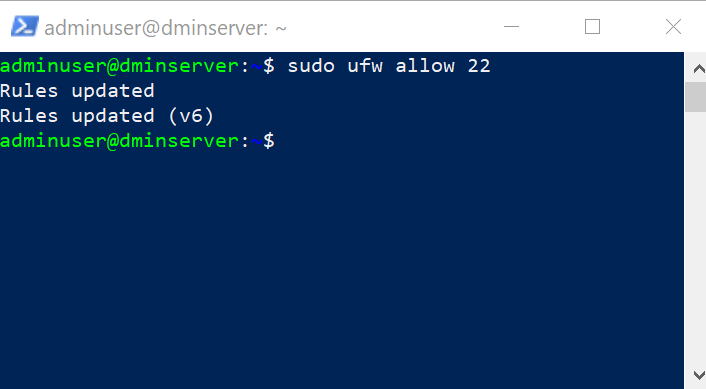
Ubuntu comes with a built-in firewall called UFW (Uncomplicated Firewall). UFW allows you to define rules for incoming and outgoing traffic, effectively controlling which ports are open. To open a port, you would use a command like `sudo ufw allow 22` to allow SSH traffic on port 22.
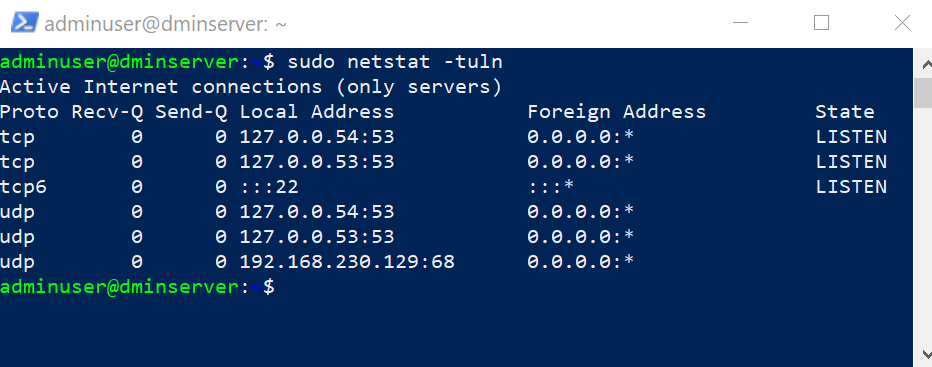
2. Checking Open Ports:
You can use the `netstat` or `ss` command in the terminal to check which ports are currently open and established connections. For example, `sudo netstat -tuln` will display a list of open ports along with their corresponding applications.
3. Closing Unnecessary Ports:
It’s best practice to close ports that are not actively being used. Leaving unnecessary ports open increases the potential attack surface for malicious actors. You can do this using UFW by running commands like `sudo ufw deny 135/tcp` to block port 135 for TCP traffic.
4. Port Scanning:
Regularly scanning your system’s open ports using tools like `nmap` can help you identify any unexpected open ports or potential vulnerabilities.
5. Application Configuration:
Some applications might require you to configure which port they should use for communication. This is common for services like web servers, email servers, and database servers.
Security Considerations:
Principle of Least Privilege: Only open the ports that are necessary for your system’s functionality. Avoid opening ports for services that you don’t explicitly need.
Regular Updates: Keeping your Ubuntu system up to date ensures that security patches are applied, reducing the risk of exploits targeting open ports.
Strong Authentication: For services like SSH, consider using key-based authentication rather than just passwords. This adds an extra layer of security to the communication process.
Network Segmentation: If possible, segment your network to isolate critical services from less secure areas, reducing the potential impact of a breach.
Conclusion:
Understanding and managing open ports in Ubuntu 2022 is crucial for both security and functionality. By following best practices, regularly auditing your open ports, and staying informed about potential vulnerabilities, you can create a more secure and efficient computing environment. Remember, while open ports facilitate communication, they also present potential risks, so always approach port management with a security-first mindset.
Open ports in Ubuntu 2022
1. Why should I care about open ports on my Ubuntu system?
2. How can I determine which ports are open on my Ubuntu system?
You can use the netstat or ss commands in the terminal to list open ports and established connections. For example, running sudo netstat -tuln will display a list of open ports along with their corresponding protocols (TCP/UDP) and associated applications. This helps you identify which services are actively listening for incoming connections.
3. Are there default open ports in Ubuntu that I should be aware of?
Ubuntu, like many operating systems, has some default open ports for common services. For instance, SSH typically uses port 22, while web servers use port 80 (HTTP) and 443 (HTTPS). These ports might be open by default to ensure basic functionality, but it’s a good practice to review and close any ports that are not needed for your specific use case. Unnecessary open ports increase the attack surface of your system.
4. How can I improve the security of open ports on my Ubuntu system?
There are several steps you can take to enhance the security of open ports:
-
Firewall Configuration: Use the UFW firewall to control incoming and outgoing traffic. Only allow necessary ports and deny the rest.
-
Regular Updates: Keep your system updated with the latest security patches. Vulnerabilities in services that use open ports are often patched in updates.
-
Port Knocking: Consider implementing port knocking, where a sequence of connection attempts to specific ports must be made before a hidden service is accessible. This adds an extra layer of security.
-
Intrusion Detection/Prevention Systems (IDS/IPS): Implementing an IDS/IPS can help monitor and block suspicious network activity, protecting your open ports from potential threats.
-
Strong Authentication: For services like SSH, use key-based authentication to prevent unauthorized access even if the port is open.
-
Port Forwarding: If you’re behind a router, configure port forwarding only for the necessary ports and avoid exposing all ports to the internet.