Changing the SSH port in Ubuntu Linux can enhance security by making your server less susceptible to automated attacks. By default, SSH listens on port 22. Switching to a non-standard port is a straightforward process that can add an extra layer of obscurity to your server. In this guide, we’ll walk through the process of changing the SSH port in Ubuntu step-by-step.
Why Change the SSH Port?
By default, SSH (Secure Shell) uses port 22. This well-known default port can be a target for brute-force attacks, where attackers try to guess usernames and passwords. Changing the SSH port is one of the simplest yet effective ways to reduce the chances of an automated attack.
While changing the port won’t stop a determined hacker, it can prevent many automated bots and scans from detecting your SSH service, providing an additional layer of security. Let’s see how to do it.
Step 1: Choose a New SSH Port Number
Before making any changes, decide on a new port number. Ideally, pick a number that is not already in use and higher than 1024. Any port number above 1024 is considered non-reserved and is less likely to conflict with other services.
For example, you can choose port 2222, 2323, or something similar.
Step 2: Modify the SSH Configuration File
The SSH configuration file (sshd_config) controls various aspects of the SSH service, including the port number. To modify it, follow these steps:
- Open the SSH Configuration File:
Use a text editor like nano to edit the configuration file:

sudo nano /etc/ssh/sshd_config
- Find the
#Port 22 Line:
Look for the line that starts with #Port 22. This line is commented out by default, meaning the SSH server will use the default port 22.
- Uncomment and Change the Port Number:
Remove the # and change the port number to your desired port. For example, to change the port to 2222, modify the line as shown below:

- Save and Exit:
Save the file by pressing CTRL + X, then Y to confirm, and Enter to exit.
Step 3: Adjust the Firewall Rules
If you are using ufw (Uncomplicated Firewall) or iptables, make sure to allow traffic on the new port. For example, if you changed the SSH port to 2222, you can allow it with:
For ufw Users:

For iptables Users:
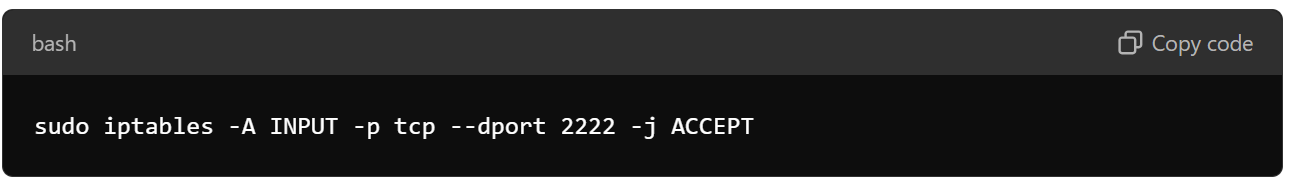
sudo iptables -A INPUT -p tcp --dport 2222 -j ACCEPT
After adding the new rule, you can remove the rule for port 22 if you want:

sudo ufw delete allow 22/tcp
Or, for iptables:
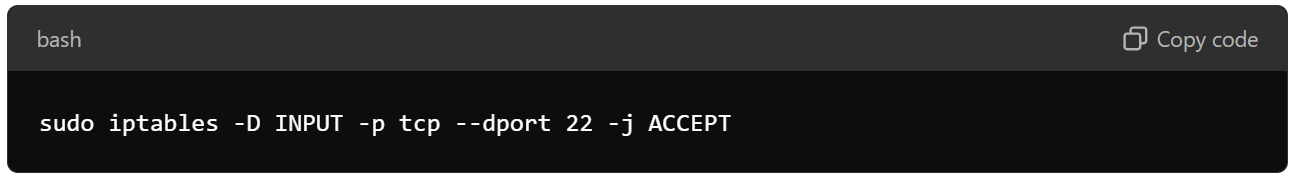
sudo iptables -D INPUT -p tcp --dport 22 -j ACCEPT
Step 4: Restart the SSH Service
After modifying the configuration file and adjusting the firewall rules, restart the SSH service to apply the changes:
sudo systemctl restart ssh
This command will restart the SSH daemon with the new configuration. It’s crucial to keep your current SSH session open until you verify that the new port works correctly.
Step 5: Test the New SSH Port
Open a new terminal window and try to connect to your server using the new port. For example, if you set the port to 2222, use the following command:
ssh username@your_server_ip -p 2222
Replace username with your SSH username and your_server_ip with the IP address of your server.
If the connection is successful, then you have successfully changed the SSH port.
Step 6: Update Any Automation or Configuration Files
If you have automated scripts, configuration management systems, or SSH configuration files that connect to this server, don’t forget to update them to use the new port.
For example, if you use the ~/.ssh/config file, add an entry for your server like this:
Host myserver
HostName your_server_ip
User username
Port 2222
This makes it easier to connect using the ssh myserver command instead of specifying the port every time.
Step 7: Optional – Disable the Default SSH Port (Port 22)
If you still see Port 22 defined in your configuration file, it’s best to disable it to ensure that only the new port is used. After confirming that your new SSH port is working, comment out or remove the line that specifies Port 22 in sshd_config.
Restart the SSH service again:
sudo systemctl restart ssh
Conclusion
Changing the SSH port is a simple yet effective way to reduce the chances of automated attacks and brute-force attempts. While it’s not a foolproof security measure, it adds an extra layer of protection, making your server less visible to opportunistic attackers.
After changing the SSH port, remember to update your firewall rules and document the new port for future reference. As always, use strong passwords, consider disabling password-based logins in favor of SSH keys, and keep your system updated.
By following this guide, you’ve taken an important step toward securing your Linux server. Happy administering!
Additional Security Tips
- Use SSH Keys: Consider using SSH keys for authentication instead of passwords.
- Disable Root Login: Set
PermitRootLogin no in sshd_config to disable direct root logins.
- Enable Fail2Ban: Use Fail2Ban or similar tools to automatically ban IP addresses that show malicious behavior.
With these steps, your SSH setup should be more secure. Keep exploring other methods to enhance your server’s security posture.






